You just have to set your letters and symbols to generate easy to remember but hard to guess passwords.
**Don't Worry We Don't Save Your Password In Any Stage.🔑 Password Generator ~ Strong, Secure, Random, & Unique Passwords
The Best Secure Password Generator for FREE. Generate Phrase password fast.
Generate random password within a second. You just have to set your letters and symbols to generate easy to remember but hard to guess passwords.
To prevent your password from being hacked through social engineering, brute force, or dictionary methods, and to keep your online accounts secure, here are some things to consider:
How to generator password quickly?
It is so simple. Just select the options that you want to include in your password and press the Generate button.
You will see a secure strong password instantly. Don't worry we never save the generated password in any way.
How to generate password of different characters
Youc can create a password os any characters from 1 to 20. You can do this by slecting the passord length meter.
How to use this Password Generator?
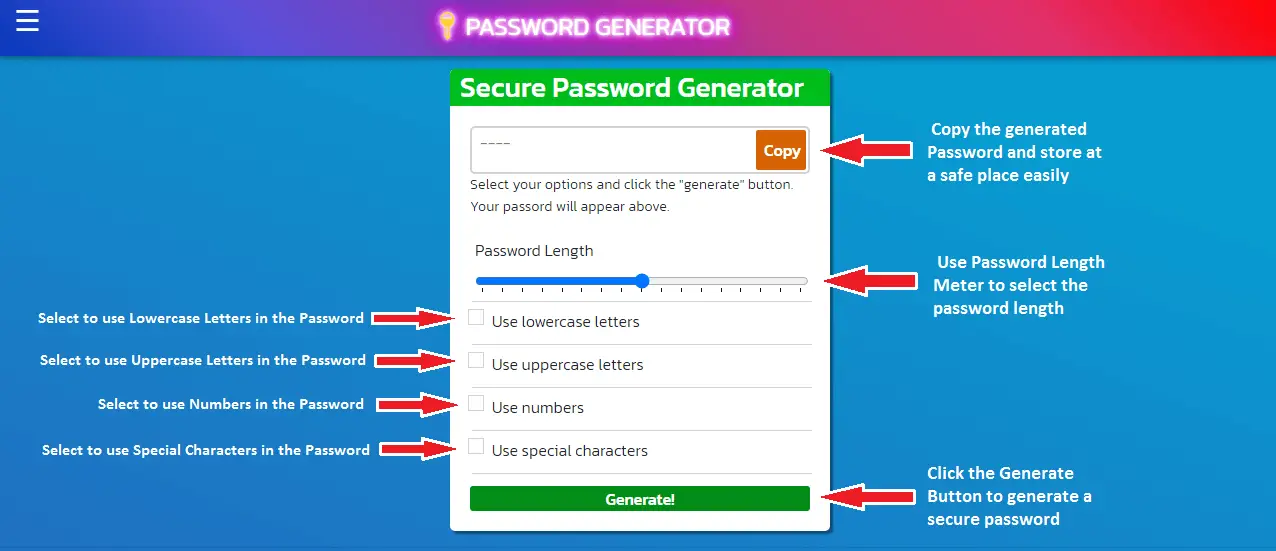
Why use a password generator?
It is always recomended to generate a unique passowrd everytime you need. Your passwords should not be same for different platforms.
Using a password generator is recommended because it can create strong and unique passwords that are difficult to guess or crack, helping to protect your online accounts from unauthorized access and potential security breaches. Randomly generated passwords typically include a mix of upper and lower case letters, numbers, and special characters, which can make them more secure than passwords that are easy to guess or use common words or phrases. Additionally, using a password manager with a password generator can make it easier to manage and store your passwords securely.
Use this Free Paswword Generator online to create a unique and secured password easily. Thios tool is useful for generating daily passwords.
What is special character password?
A special character password is a password that includes one or more special characters in addition to letters and/or numbers. Special characters are non-alphanumeric characters such as !, @, #, $, %, etc.
Using special characters in a password can increase its complexity and make it more difficult to guess or crack. However, it's important to note that a strong password should not solely rely on special characters, but also include a mix of upper and lower case letters, numbers, and be of sufficient length.
For example, a password such as "P@ssw0rd!" may be more secure than "password", but a longer passphrase such as "correct horse battery staple" would be even stronger.
What is encrypted password?
An encrypted password is a password that has been transformed into an unintelligible form using an encryption algorithm. This transformation is done for security reasons, as it makes it more difficult for an unauthorized person to access the password and the associated account or system.
When a user creates a password, it is encrypted and stored in a database or other storage medium in its encrypted form. When the user enters the password for authentication, the system encrypts the entered password and compares it to the stored encrypted password.
If the two encrypted values match, the user is granted access. Encryption is a crucial aspect of password security, and various encryption algorithms are used depending on the system and its security requirements.
What do do you mean by Unique Password?
A unique password is a password that is not used for any other account or system. Using a unique password for each account or system is important for security, as it helps to prevent unauthorized access in case a password is compromised or leaked from one account.
When passwords are reused, a single security breach can lead to multiple accounts being compromised, which can have serious consequences. Using unique passwords for each account can be challenging to remember, but using a password manager can make it easier to manage and store unique passwords securely.
Why we need an Unique Password each time?
It is important to use a unique password each time because reusing passwords across multiple accounts can make it easier for attackers to gain unauthorized access to sensitive information. If a password is compromised or leaked from one account, attackers can use it to try and gain access to other accounts that use the same password. This is known as password reuse or credential stuffing, and it is a common tactic used by cybercriminals to exploit weak or reused passwords.
Using a unique password for each account can greatly reduce the risk of unauthorized access in case of a data breach or security incident. It may be challenging to remember multiple passwords, but using a password manager can make it easier to create and store unique passwords securely. Additionally, enabling two-factor authentication can provide an additional layer of security to help protect your accounts.
Best Practices To Keep Your PASSWORD SECURE
1. Avoid using the same password, security questions, and answers for many important accounts.
2. Use a password that contains at least 16 characters, at least one number, one uppercase letter, one lowercase letter, and a special symbol.
3. Do not use the names of your family, friends, or pets in your password.
4. Do not use zip code, house number, telephone number, date of birth, ID card number, social security number, etc. in your password.
5. Do not use dictionary words in your password. Examples of secure passwords: ePYHc ~ dS *) 8 $ + V- ', qzRtC {6rXN3N \ RgL, zbfUMZPE6`FC%) sZ. Examples of weak passwords: dsgfdjsg12345, safgsrgKKJ, 1234567890, 987654321, nortonpassword.
6. Do not use two or more identical passwords that are identical to most of their characters, e.g. B. ilovefreshflowersMac, ilovefreshflowersDropBox. Since one of these passwords is being stolen, it means that all of these passwords will be stolen. went.
7. Do not use anything that can be cloned (but cannot be changed) as a password; B. your fingerprint.
8. Do not allow your web browser (Firefox, Chrome, Safari, Opera, IE, Microsoft Edge) to save your password as any passwords saved in the web browser can be easily exposed.
9. Do not enter important accounts on other people's computers or when connected to public Wi-Fi hotspots, Tor, free VPNs, or web proxies.
10. Do not send confidential information online over unencrypted (e.g. HTTP or FTP) connections because messages on these connections can be intercepted with very little effort. If possible, you should use encrypted connections such as HTTPS, SFTP, FTPS, SMTPS, IPSec.
11. When traveling, you can encrypt your Internet connection before you leave your laptop, tablet, mobile phone or router. For example, you can set up a private VPN (with MS-CHAP v2 or stronger protocols) on your own server (home computer, dedicated server or VPS) and connect to it. Alternatively, you can set up an encrypted SSH tunnel between your computer and your own server and configure Chrome or Firefox to use the sock proxy. However, if someone captures your data transmitted between your device (e.g. laptop, iPhone, iPad) and your server with a packet sniffer, they will not be able to steal your data and password from encrypted streaming data.
12. How secure is my password? You may think that your passwords are too secure and difficult to hack. However, if a hacker stole the MD5 hash of your username and password from a company's server and the hacker's rainbow table contains that MD5 hash, your password will be cracked quickly.
To check the strength of your passwords and find out whether they are in popular rainbow tables, you can change your passwords to MD5 hashes in the MD5 hash generator and then deposit these passwords with the online MD5 decryption service. Decrypt your password. For example, your password is "0123456789A". If you use the brute force method, it may take about a year to crack your password. However, if you send the MD5 hash (C8E7273CD035B23BB9C0F1F954DFF5B3) to your encryption website let's decrypt it. How long will it take to crack it? You can test yourself.
13. It is advisable to change your password every 10 weeks.
14. It is recommended that you memorize some master passwords, save the other passwords in a plain text file, and encrypt that file using 7-Zip, GPG, or bit encryption software such as BitLocker or password management software. Manage your passwords with.
15. Encrypt and secure your passwords in different locations. If you've lost access to your computer or account, there's a quick way to get your password back.
16. Activate 2-step authentication if possible.
17. Don't save your important passwords in the cloud.
18. Directly access important websites (e.g. PayPal) via bookmarks. Otherwise, check the domain name carefully. Check the website's popularity using the Alexa toolbar to make sure your password is entered - there is no phishing site yet.
19. Protect your computer with a firewall and anti-virus software, block all incoming connections and all unnecessary outgoing connections with the firewall. Only download software from reputable websites and, if possible, double-check the MD5 / SHA1 / SHA256 checksum or the GPG signature of the installation package.
20. Keep track of your device's operating system (such as Windows 7, Windows 10, Mac OS X, iOS, Linux) and the web browser (such as Firefox, Chrome, IE, Microsoft Edge) (such as Windows PC, Mac PC, iPhone , iPad) for), Android Tablet) is up to date by installing the latest security updates.
21. If you have important files on your computer that others can access, check for hardware keyloggers (such as wireless keyboard sniffers), software keyloggers, and hidden cameras if you see them necessary.
22. If you have a WIFI router at home, you can find out the password you entered (at your neighbour's house) by recognizing your fingers and hand gestures as moving your fingers as the WIFI signal will change. Hand. In such cases, you can use the onscreen keyboard to enter your password. It would be safer if that virtual keyboard (or soft keyboard) changes layout every time.
23. Turn off your computer and mobile phone when you leave them. Encrypt the entire hard drive with LUKS or similar devices before inserting important files and if necessary physically destroy the hard drives of your old devices.
25. Access important websites in private or incognito mode, or use a web browser to access important websites. Use each other to access other websites. Or access unimportant websites and install new software in a virtual machine created with VMware, VirtualBox or Parallels.
26. Use at least 3 different email addresses. Use the first one to receive email from major websites and apps like PayPal and Amazon. Use the other to receive email from unimportant websites and apps. Use a third (separate) email provider like Outlook and Gmail to get your password reset email if the former (like Yahoo Mail) is hacked.
27. Use at least 2 different phone numbers. Do not give anyone else the phone number they will use to receive the verification code text message.
28. Do not click links in email or text messages, click or reset your password unless you know those messages are not fake.
29. Do not share your password with anyone in an email.
30. It is possible that a software or app that you downloaded or updated has been modified by hackers. You can avoid this problem by not installing this software or app for the first time unless it has been released to fix. You can use web-based apps instead, which are more secure and portable.
31. Use caution when using online insert tools and screen capture tools. Don't let them upload your passwords to the cloud.
32. If you are a webmaster, do not store users' passwords, security questions, and answers as plain text in the database. You should store the salty (SHA1, SHA256, or SHA512) hash values of these strings instead. It is recommended that you generate a unique random salt string for each user. In addition, it is a good idea to log the user's device information (e.g. operating system version, screen resolution, etc.) and save salty hash values of them when trying to log in with the correct password again.The device information does not match what was previously saved Information match. Allow this user to verify their identity by entering a different verification code sent via SMS or email.
33. If you are a software developer, you should publish an update package that was signed with a private key using GnuPG and check its signature with a previously published public key.
34. To protect your online business, you should register your own domain name and set up an email account with that domain name. Then you won't lose your e-mail account and all your contacts, because your mail can host your server anywhere, your e-mail account cannot be deactivated by the e-mail provider.
35. If an online shopping site only allows credit card payments, consider using a virtual credit card instead.
36. When you leave your computer, close your web browser. Otherwise, cookies can easily be intercepted with a small USB device, which can bypass the two-step verification on other computers. You can be logged into your account with stolen cookies.
37. Delete and delete faulty SSL certificates in your web browser. Otherwise, you cannot guarantee the confidentiality and integrity of the HTTPS connections that use these certificates.
38. Encrypt the entire system partition. Otherwise, turn off the paging file and hibernation feature as you can find your important documents in the pagefile.size and hibernate.size files.
39. To prevent brute force login attacks for your dedicated server, VPS server or cloud server, you can install intrusion detection and prevention software such as LFD (Log Failure Daemon) or Fail2Bain.